WordPress is one of the most popular content management systems (CMS) in the world today & powers more than 40% of the top websites on the internet.
It is no surprise why hackers attempt to gain illegal access using various vulnerabilities present in the WordPress ecosystem.
WordPress is open-source and thus allows anyone to inspect its code and make changes as seen fit.
Hackers have exploited this open-source nature of the CMS for years and formulated ways to use vulnerabilities they detect.
Table of Contents
- How Secure is WordPress?
- Why do WordPress sites get hacked?
- Reason #1: Not changing the WordPress admin username / using “admin” as the default
- Reason #2: Weak / Leaked Passwords
- Reason #3: Outdated WordPress / Themes / Plugins
- Reason #4: Outdated Versions of PHP
- Reason #5: Using Nulled/Pirated Theme or Plugin
- Reason #6: Shared Hosting
- Reason #7: Non-SSL website
- Reason #8: Using FTP instead of SFTP/SSH
- Why it’s essential to keep your website secure?
According to the WordFence threat intelligence team, there are approximately 168,000+ attacks per minute on WordPress websites.
This problem has only increased over the years as more and more businesses continue to create their online presence using WordPress.
In this lesson, we will be exploring the top 8 reasons why WordPress sites get hacked and how they can be prevented.
But first…
How Secure is WordPress?
WordPress is open-source and was started by a community of developers. It is maintained by approximately 400-500 core contributors who ensure that issues are patched regularly.
With the amount of expertise, knowledge, experience, and resources backing WordPress, it would be one of the most secure content management systems (CMS) in the world, right?
Having existed for almost 18 years, WordPress has been continuously updated to industry-standard security levels.
Without any third-party plugins or themes, the WordPress core software is secure enough to handle any code-related attacks.
Why do WordPress sites get hacked?
While the WordPress core software is secure enough to handle common code-related attacks, the CMS is prone to the same issues as any other software.
WordPress does not show any signs of being prone to hacks by itself.
Instead, hackers exploit vulnerabilities in plugins and themes present on a WordPress site and poor user practice to make it vulnerable to malicious attacks.
Most WordPress experts agree that almost 90% of hacked/vulnerable WordPress sites are due to misconfiguration and outdated plugins and themes.
Here are the top 8 reasons why WordPress websites can get hacked:
Reason #1: Not changing the WordPress admin username / using “admin” as the default
WordPress users have made it a regular practice to assign “admin” as the username for the default account with administrative privileges when setting up WordPress.
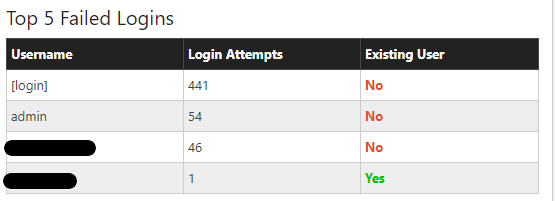
This practice is what hackers have exploited to gain access to WordPress sites more easily.
Once an attacker figures out your username, he is just one step behind from cracking your password (assuming you do not have 2-factor authentication enabled).
It is vital to use a unique username when creating your default admin account.
If possible, it’s better not to publish posts using your admin account. This way, your admin username will stay hidden from the public.
Reason #2: Weak / Leaked Passwords
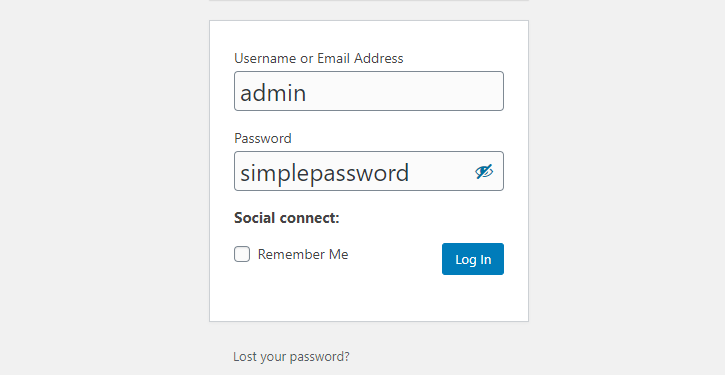
When it comes to creating passwords, many WordPress users stick with easy-to-remember passwords that they feel are secure enough, i.e., “myblogname12345”.
Some even go hyper descriptive and create passwords like “myblognameadmin” to make sure they couldn’t forget it.
Creating a password you cannot remember should be the standard here.
Think about it, what would be easier for an attacker to figure out?
A descriptive password you can remember or a random password that you struggle to remember?
That’s right – you should use a random password instead of a memorable one.
The basic rules of creating a secure password are simple: use a combination of capitalized and lowercase letters, numbers, and symbols.
Never to go descriptive – be as random as possible.
Another mistake many WordPress users make is using the same password they’ve used for other websites for their WordPress admin account.
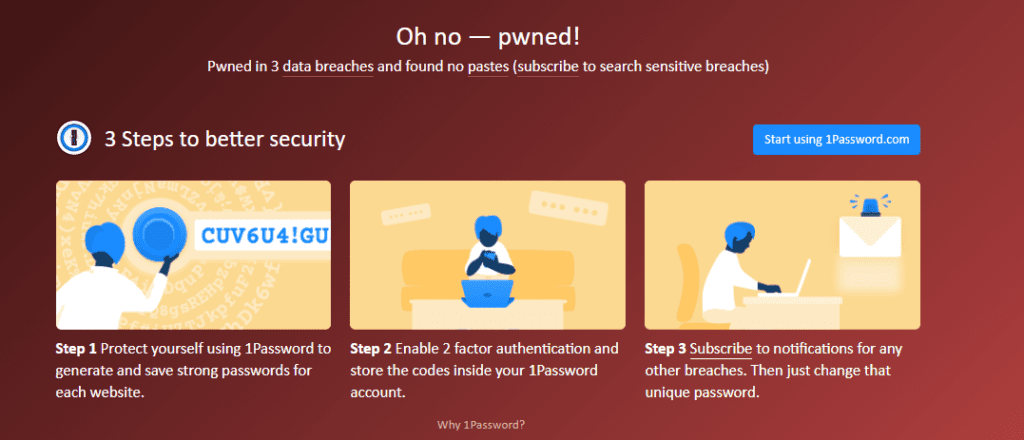
A quick email check on Haveibeenpwned will open your eyes to why this is a bad practice that might get all your online accounts (not just WordPress) hacked.
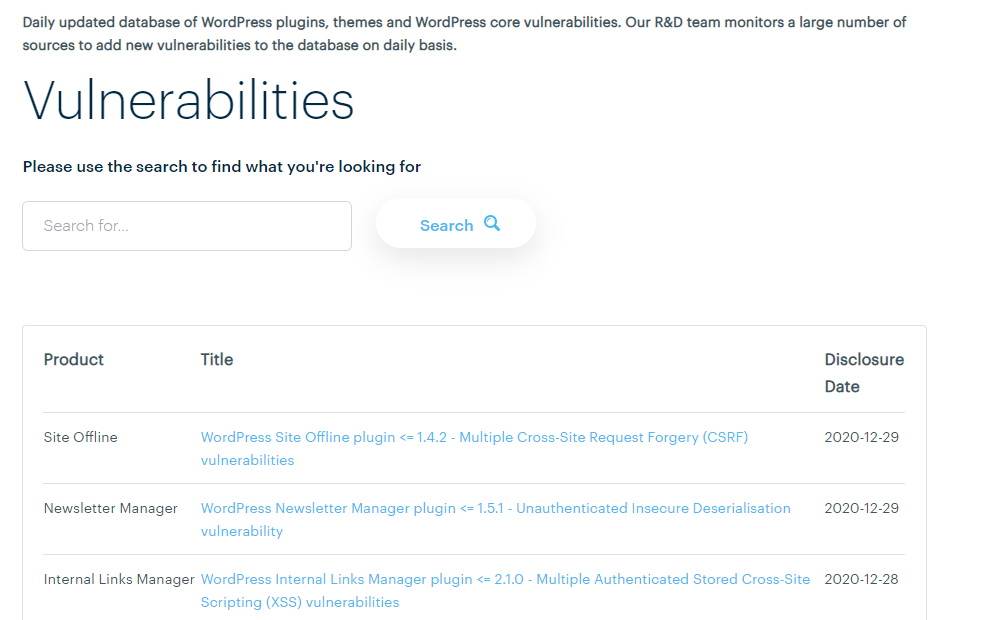
Reason #3: Outdated WordPress / Themes / Plugins
Want to get your WordPress website hacked anytime soon?
Leave all of your plugins and themes outdated,
With websites like WPscan and ThreatPress reporting vulnerabilities in WordPress themes and plugins daily, keeping your plugins or themes outdated for even a day could expose you to some serious security breaches.
To combat this security issue, the WordPress team (as of 5.5) introduced an optional auto-update feature for WordPress themes & plugins, which can save you a lot of trouble.
Suppose you don’t have the auto-update feature enabled. In that case, you should manually update your plugins and themes within 24 hours of an update was released.
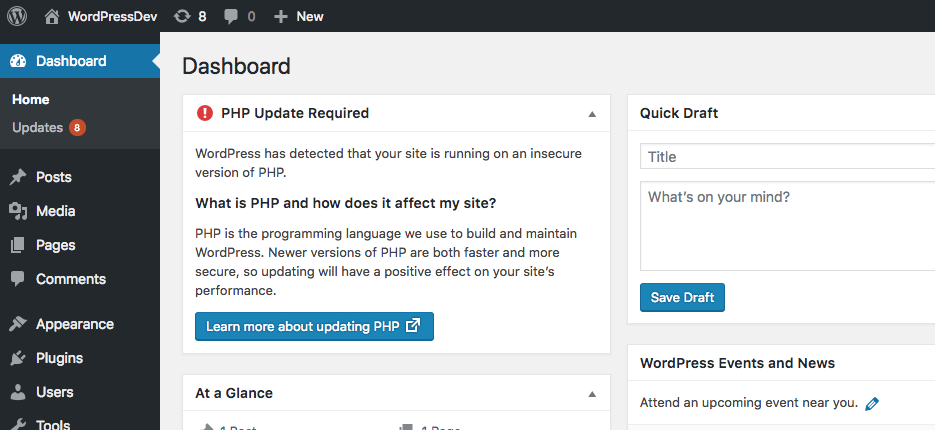
Reason #4: Outdated Versions of PHP
Like every technology out there, support is dropped for older versions when new versions are released.
PHP is currently at its version 8, but many hosting companies still use older versions of the technology to power PHP-dependent applications like WordPress.
The problem with using an outdated version of PHP (or any technology for that matter) lies in the fact that newly discovered vulnerabilities might not be patched.
Hackers will always exploit these vulnerabilities to gain access to your WordPress site. Often, they may be successful.
It is crucial to use a PHP version compatible with the WordPress version you are running.
Reason #5: Using Nulled/Pirated Theme or Plugin
A Nulled script is any script (a paid one usually) where hackers tamper its code to enable illegal usage.
Premium scripts like WordPress themes and plugins come with a license key on purchase.
A nulled theme or plugin has a piece of code removed or added to bypass the license checker and enable all paid features for free.
Using nulled theme or plugin is illegal. About 90% of nulled themes/plugins available today are distributed through forums, offshore hosted blogs, and so-called GPL stores.
Hackers intentionally invest time and money into nulling popular WordPress themes and plugins. They added malicious code that cannot be easily detected by antivirus software.
They distribute these compromised nulled items on forums and blogs worldwide and wait for unsuspecting WordPress users to download and install them on their servers.
Once in use, these hackers will now have backdoor access to the WordPress system.
No form of security can protect you if hackers are already present within your system.
Reason #6: Shared Hosting
Poor performance is not the only disadvantage of using a shared host for WordPress. Sharing a single server instance with other websites exposes your WordPress site to various security attacks.
Once a hacker gains access to a shared server from any of its members, they are just a few steps away from accessing every other member-hosted site.
Hackers can wreak havoc on your website by running scripts that can quickly wipe out an entire server.
I have explained fully in the previous topic why shared hosting is bad for a WordPress site.
I’m not going to repeat myself here again.
Hosting on a cloud server or managed WordPress hosting is more preferable and secure compared to shared hosting.
A cloud server or any other higher tier hosting option is more equipped to handle such attacks because of the way they are configured (partitioning & privacy).
Reason #7: Non-SSL website
When users interact with your website, it is essential to encrypt all requests from and to your website’s server.
HTTP is the default protocol every domain uses. It has several known risks, especially when receiving and returning sensitive data like passwords and credit card details.
Using HTTP for a WordPress site is a bad idea. WordPress is built to handle sensitive data, from the login page to fulfilling eCommerce orders.
A hacker using sniffing techniques can grab any data being transferred from the protocol’s header information.
Things like passwords, usernames, and sensitive data can easily be exposed.
It is important to use HTTPS by adding an SSL certificate to act as an intermediary between your server and client browsers.
It provides encrypted and signed connections by using a certificate authority to authenticate your site.
There is a certificate authority that provides free SSL certificates for websites, called Let’s Encrypt.
If you’re using Cloudways for your WordPress site, you can easily connect your website with a free SSL certificate issued via Let’s Encrypt.
Reason #8: Using FTP instead of SFTP/SSH
Just like HTTP, FTP is also just as insecure.
It relies on clear-text usernames and passwords for authentication, and there is no encryption. This exposes FTP to basic attack methods like sniffing and spoofing.
This is a standard method hackers use to access servers and tempered with WordPress installations.
Using alternatives like SSH or SFTP will completely shut down any form of vulnerability known with File transfer as they are encryption-enabled.
If you’re still using FTP for file transfer, make sure you switch to SFTP immediately.
Why it’s essential to keep your website secure?
Keeping your website secure shouldn’t be treated as a one-time or peripheral task.
Without first securing your WordPress site, you are practically inviting attackers to steal sensitive information and put your website users at risk.
Imagine running an eCommerce store without any proactive security strategy.
An attacker could gain access and steal information like credit card details, which can ultimately damage your customer’s trust in your business.
In short, nobody wants to have anything to do with a flimsy WordPress site.
Thus, it’s crucial to invest time and money into making sure there are no loose ends.
In the next lesson, I’ll show you the 12-steps checklist to protect your WordPress Site from hackers.
If you found this lesson helpful, please share it by clicking any social media icons at the bottom of the page.

